In today’s interconnected world, safeguarding your personal information is more critical than ever. Your phone, serving as a gateway to your digital life, requires robust protection against unauthorized access. This comprehensive guide delves into the world of two-factor authentication (2FA) security, a crucial layer of defense that significantly strengthens your phone’s security posture. Learn how 2FA acts as a shield, protecting your sensitive data from cyber threats and bolstering your overall online security.
Two-factor authentication, often abbreviated as 2FA, adds an extra layer of security beyond your standard password. By requiring a second form of verification, 2FA makes it exponentially more difficult for unauthorized individuals to access your accounts, even if they manage to obtain your password. This guide will explore the various types of 2FA, including authenticator apps, SMS-based 2FA, and hardware tokens, providing you with the knowledge to choose the best 2FA method for your individual needs. Discover how to effectively shield your phone and enhance your digital security with this comprehensive guide to 2FA.
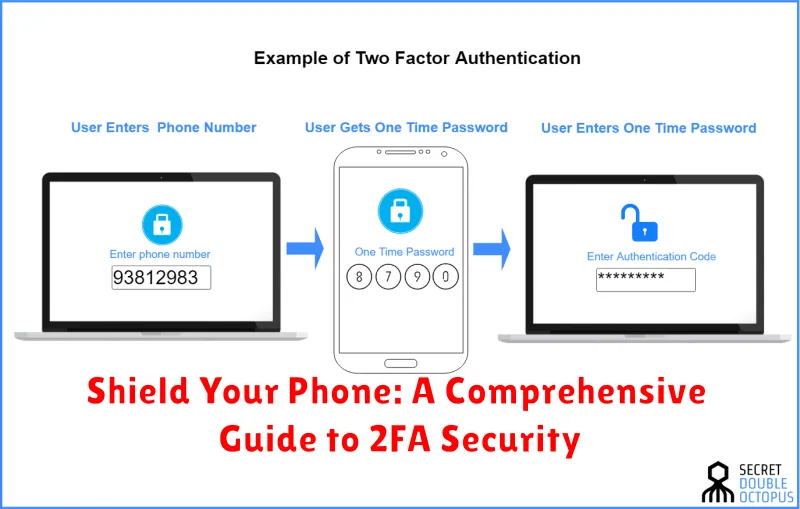
Understanding Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a security measure that adds an extra layer of protection to your online accounts, including those on your phone. It goes beyond just a username and password, requiring a second form of verification to confirm your identity.
Think of it like a double lock on your front door. Your password is the first lock, but 2FA acts as the deadbolt, making it significantly harder for unauthorized access even if someone manages to obtain your password.
2FA works on the principle of requiring something you know (your password) and something you have (like a code from your phone or a biometric scan). This combination makes it much more difficult for hackers to gain access, as they would need both pieces of information.
Why 2FA is Essential for Your Phone’s Security
Your phone holds a treasure trove of personal information, from banking details and private conversations to access to social media and email accounts. Protecting this data is paramount, and two-factor authentication (2FA) provides a crucial layer of security against unauthorized access.
Imagine your password being compromised through phishing or a data breach. With 2FA enabled, a thief attempting to log into your accounts would require a second factor, something beyond just the password. This second layer acts as a gatekeeper, effectively blocking unauthorized access even if your password is known.
2FA makes it significantly harder for hackers to gain access to your accounts, even if they manage to steal your password. This added protection safeguards your sensitive information and mitigates the risk of identity theft, financial loss, and reputational damage.
Different Types of 2FA Methods
Two-factor authentication utilizes various methods to verify your identity. Understanding these different types can help you choose the most suitable option for your security needs.
SMS-based 2FA
This common method sends a unique code to your phone via text message. While convenient, it’s considered less secure due to potential vulnerabilities like SIM swapping.
Authenticator Apps
Apps like Google Authenticator or Authy generate time-based one-time passwords (TOTPs). These apps offer enhanced security compared to SMS.
Hardware Security Keys
Physical keys, often connected via USB or NFC, provide the strongest form of 2FA. They are highly resistant to phishing and other attacks.
Push Notifications
Some services offer 2FA through push notifications to a trusted device. You simply approve or deny the login attempt.
Biometrics
Using your fingerprint, face, or other biometric data can serve as a second factor. This method is often integrated directly into devices.
Setting Up 2FA on Your Phone: A Step-by-Step Guide
Enabling 2FA typically involves a straightforward process, though it may vary slightly depending on the app or service. Here’s a generalized guide:
Step 1: Locate the 2FA Settings
Within the app or service, navigate to the security or account settings. Look for an option labeled “Two-Factor Authentication,” “2FA,” or similar.
Step 2: Choose Your Authentication Method
Select your preferred 2FA method. Common options include authenticator apps (like Google Authenticator or Authy), SMS codes, or security keys. Consider the security and convenience of each option.
Step 3: Link Your Phone
If using an authenticator app, you’ll be prompted to scan a QR code displayed on the screen. If opting for SMS, enter your phone number.
Step 4: Verify and Save
Enter the verification code generated by your chosen method to confirm the setup. Some services provide backup codes – store these securely in case you lose access to your primary authentication method. These codes are crucial for account recovery.
Best Practices for Managing 2FA
Implementing 2FA is a significant step towards bolstering your security. However, managing it effectively is equally crucial. Here are some best practices to consider:
Choose Strong and Diverse Authentication Methods
Avoid relying solely on SMS-based 2FA. Explore alternative methods like authenticator apps or security keys for enhanced protection. Diversify your 2FA methods across different accounts to minimize the impact of a single point of compromise.
Keep Your Recovery Codes Secure
Recovery codes are your lifeline if you lose access to your primary authentication method. Store them securely offline, preferably in a physical format like a printed document or a password manager.
Regularly Review Your 2FA Settings
Periodically review your enrolled 2FA methods. Ensure your contact information and recovery options are up-to-date. Deactivate any outdated or unused authentication methods promptly.
Be Wary of Phishing Attacks
Never share your 2FA codes or recovery information with anyone, including individuals claiming to be technical support. Legitimate services will never request this information.
Troubleshooting Common 2FA Issues

While 2FA significantly enhances security, occasional hiccups can occur. This section addresses common issues and provides solutions.
Lost or Broken Device
Losing your phone or having it break can disrupt 2FA access. Backup codes are crucial in these situations. Store them securely offline, separate from your device. Contact your service provider if you haven’t generated backup codes.
Authenticator App Problems
If your authenticator app malfunctions, try reinstalling it. If the issue persists, you may need to re-sync your accounts using your recovery codes. Remember, never delete your authenticator app without first disabling 2FA on associated accounts.
Receiving Codes Late
Delayed codes can stem from network issues. Check your connection. If stable, verify your phone number or email address associated with the 2FA service.
Staying Ahead of the Curve: Advanced 2FA Tips

While setting up 2FA is a significant step towards enhanced security, consider these advanced strategies to further fortify your defenses:
Hardware Security Keys
Consider investing in a physical security key. These devices offer the strongest form of 2FA, as they are immune to phishing attacks and malware.
2FA App Management
If you use a 2FA app, ensure you back up your app’s secrets securely. Losing access to your 2FA app can lock you out of your accounts. Explore options like encrypted backups or dedicated password managers.
Account Recovery Options
Configure robust account recovery methods. While 2FA enhances security, losing your primary authentication method can be problematic. Ensure your recovery options are up-to-date and secure.
Regular Audits
Periodically review your enrolled 2FA methods for each account. Remove any outdated or unused methods to minimize potential vulnerabilities.