Tired of incessant robocalls interrupting your dinner? Exasperated by the endless stream of spam text messages clogging your inbox? You’re not alone. Unwanted calls and messages are a pervasive problem, impacting millions worldwide. This comprehensive guide provides practical strategies to help you stop spam in its tracks, reclaiming control over your phone and your peace of mind. We’ll delve into effective methods for blocking unwanted calls and blocking spam messages, exploring everything from built-in phone features to third-party apps, and offering insights into how to identify and report these nuisances. Learn how to effectively combat spam calls and spam text, empowering yourself to take charge of your communication channels.
This guide will equip you with the knowledge and tools to effectively manage and minimize unwanted communications. We’ll explore various techniques for blocking unwanted calls and messages, covering both Android and iOS platforms. We’ll examine the telltale signs of spam calls and spam text, helping you quickly identify and filter these intrusions. From utilizing your phone’s built-in features to leveraging the power of specialized apps, we’ll cover a range of solutions to help you stop spam. Learn the best practices for protecting yourself from spam, regaining control over your digital life, and enjoying uninterrupted communication.
Identifying Spam Calls and Messages
Recognizing spam is the first step in effectively blocking it. Pay close attention to the following indicators:
Caller ID and Number Recognition
Spam calls often display suspicious caller IDs. These might include:
- Unknown or Private numbers
- Numbers that mimic your own area code and prefix (neighbor spoofing)
- Numbers that appear as a long string of digits
Content of the Call or Message
Be wary of communications that:
- Promise too-good-to-be-true prizes or offers
- Create a sense of urgency, pressuring you to act quickly
- Request personal or financial information
- Contain grammatical errors or typos
- Come from unknown senders with generic greetings
Unexpected Contact
If you haven’t initiated contact with a business or individual, be cautious about responding to their calls or messages. Legitimate organizations typically have a record of your interaction.
Using Built-in Blocking Features
Most modern smartphones and communication apps offer built-in features to block unwanted calls and messages. These tools provide a convenient first line of defense against spam. Learn to use these features effectively to manage your communications.
Call Blocking: On most smartphones, you can block individual numbers directly from your call log or recent calls list. Simply locate the offending number, select it, and choose the option to block or add to the block list. This prevents future calls from that specific number.
Message Filtering: Messaging apps often provide filtering options to separate spam messages from legitimate ones. Look for options within your messaging app’s settings to filter messages from unknown senders or to create custom filters based on keywords or phrases commonly found in spam.
Silence Unknown Callers: This feature allows you to silence calls from numbers not saved in your contacts. While not strictly blocking, it can significantly reduce interruptions from unknown or suspected spam callers. You’ll still see a record of the missed call, allowing you to review and potentially block the number later.
Exploring Third-Party Spam Blocking Apps
Beyond built-in features, a wide array of third-party apps offer advanced spam blocking capabilities. These apps often leverage extensive databases of known spam numbers and employ sophisticated algorithms to identify and filter unwanted calls and messages. They can provide a more robust defense against spam compared to basic phone features.
When choosing a third-party app, consider factors such as: caller ID identification, spam call blocking, message filtering, and community-based spam reporting. Some apps offer automatic blocking of suspected spam calls, while others provide alerts and allow you to choose how to handle them. Read reviews and compare features to find the best fit for your needs.
Privacy is paramount. Be mindful of the permissions requested by these apps. Some apps may require access to your contacts or call logs to effectively identify and block spam. Carefully evaluate the app’s privacy policy before installation to ensure it aligns with your comfort level.
Registering with the National Do Not Call Registry
A crucial step in combating unwanted calls is registering your phone numbers with the National Do Not Call Registry. This free service allows you to add your landline and mobile numbers to a database that telemarketers are required to honor. While it won’t stop all unwanted calls (such as scams, political calls, or calls from organizations you’ve recently done business with), it significantly reduces calls from legitimate telemarketers.
Registering is straightforward. You can register your number online or by calling the toll-free number. It’s important to note that registration doesn’t take effect immediately. It can take up to 31 days for telemarketers to update their call lists. After that, most telemarketing calls should cease.
Remember to re-register your numbers periodically, especially if you move or change phone numbers. Registration does not expire, but re-registering ensures your information remains current in the database.
Filtering Messages with Keywords
Filtering messages based on specific keywords can be a powerful tool in managing unwanted communications. This method allows you to automatically categorize or block messages containing pre-defined words or phrases commonly found in spam. Keywords can include loan offers, debt relief, prize notifications, or other suspicious terms.
Many email providers and messaging apps offer built-in keyword filtering. These filters can be customized to move messages to a separate folder, mark them as spam, or delete them entirely. Effective keyword selection is essential to avoid accidentally filtering legitimate messages. Start with a list of common spam terms and refine your list over time as you observe patterns in the spam you receive.
Some platforms allow you to use wildcards or regular expressions for more advanced filtering. These tools allow you to target variations of a keyword, improving the filter’s accuracy and catching slightly modified spam messages. For example, using “free*” could filter messages containing “free,” “freely,” “freedom,” etc.
Reporting Spam and Phishing Attempts
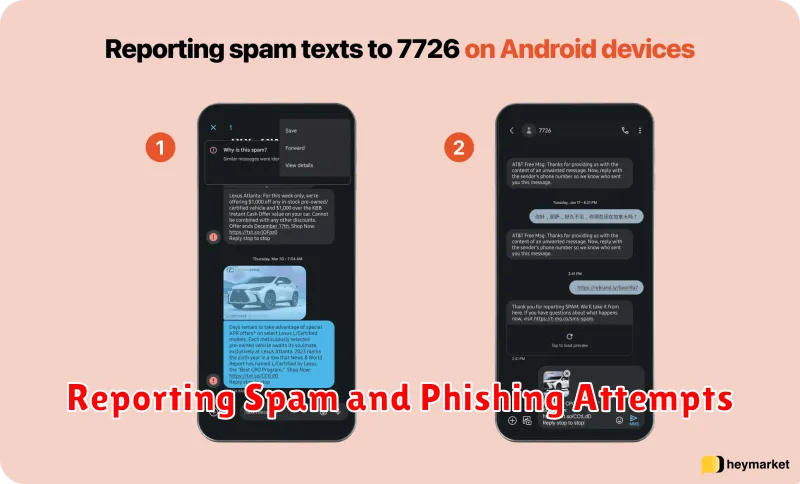
Reporting spam and phishing attempts is crucial in the fight against these intrusive and often malicious communications. By reporting these incidents, you contribute valuable data that helps authorities and service providers identify patterns, track perpetrators, and implement more effective countermeasures. Reporting also empowers you to take an active role in protecting yourself and others from future attacks.
For spam text messages, forward the message to 7726 (SPAM). This will alert your carrier to the unwanted communication. For spam emails, mark the email as spam or junk within your email client. Most email providers also have a “report phishing” option if the email attempts to fraudulently obtain your personal information.
You can also report robocalls and telemarketing calls to the Federal Trade Commission (FTC) at their website or by phone. The FTC uses this information to track trends and take action against illegal callers.
When reporting, provide as much detail as possible, including the phone number, email address, or other identifying information of the sender, the content of the message, and the date and time you received it. This information will help investigators identify and track down the source of the spam or phishing attempt.
Managing Call Forwarding and Blocking Settings
Call forwarding can inadvertently route spam calls to your phone even if you’ve blocked them directly. Review your call forwarding settings to ensure they aren’t contributing to the problem. Most smartphones allow you to access these settings through the phone app itself, typically under “Call Settings” or a similar menu.
Within your call forwarding settings, you’ll likely find options for forwarding calls always, when busy, when unanswered, or when unreachable. Carefully examine each setting. If you don’t recognize a forwarded number, disable the forwarding immediately.
Some carriers also offer advanced call blocking features directly through their services. Contact your provider to inquire about options like anonymous call blocking, specific number blocking, or even blocking calls from entire area codes. These services might involve additional fees, but they can provide a more robust layer of defense against unwanted calls.
Additionally, explore your phone’s built-in blocking settings. Many smartphones allow you to create a blacklist of numbers that will be automatically rejected. Regularly review and update this list as needed.
Protecting Your Personal Information

Protecting your personal information is crucial in minimizing the risk of spam and related scams. Spammers often leverage readily available information to target individuals more effectively. By limiting access to your data, you significantly reduce your vulnerability.
Be cautious about sharing personal details online, especially on social media platforms and unfamiliar websites. Information such as your phone number, email address, and physical address should be kept private whenever possible.
Review privacy settings on your social media accounts and adjust them to restrict who can view your information. Avoid posting sensitive data publicly, and be mindful of the information you share in online quizzes, surveys, and contests.
Regularly check your credit reports for any suspicious activity, which could indicate identity theft or unauthorized access to your personal information. Promptly report any discrepancies to the relevant credit reporting agencies.
Strong passwords are essential for safeguarding your online accounts. Use unique passwords for each account, incorporating a combination of uppercase and lowercase letters, numbers, and symbols.
Staying Vigilant Against New Spam Tactics
Spammers constantly evolve their tactics to bypass filters and exploit vulnerabilities. Staying informed about emerging trends is crucial in protecting yourself.
Be wary of new communication channels. Spam isn’t limited to calls and texts. Be cautious of unsolicited messages through social media, email, and other platforms. Verify the sender’s identity before interacting with any unexpected communication, especially if it requests personal information or prompts you to click a link.
Keep your software updated. Regularly updating your operating system and apps ensures you have the latest security patches against known vulnerabilities that spammers might exploit.
Educate yourself. Regularly review resources from reputable organizations regarding current spam and phishing techniques. This awareness will help you identify and avoid potential threats more effectively.

